Ensuring Security in AI Applications with OWASP Top 10
𝗜𝘀 𝘆𝗼𝘂𝗿 𝗔𝗜 𝗔𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝘀𝗲𝗰𝘂𝗿𝗲? 𝗗𝗶𝘀𝗰𝗼𝘃𝗲𝗿 𝗿𝗲𝗰𝗼𝗺𝗺𝗲𝗻𝗱𝗮𝘁𝗶𝗼𝗻 𝗳𝗿𝗼𝗺 𝗢𝗪𝗔𝗦𝗣 𝗧𝗼𝗽 𝟭𝟬 𝗳𝗼𝗿 𝗔𝗜 𝗮𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀.
As someone deeply involved in the 𝗔𝗜 𝗘𝗻𝗴𝗶𝗻𝗲𝗲𝗿𝗶𝗻𝗴 space, I recognize the critical importance of securing AI applications.
Exploring the security aspect has often been overlooked in the frenzy of integrating Foundation AI Models into business operations and client-facing applications since late 2022. This rapid adoption has been nothing short of remarkable. However, it has outpaced the establishment of comprehensive security protocols, leaving many AI applications vulnerable to high-risk issues.
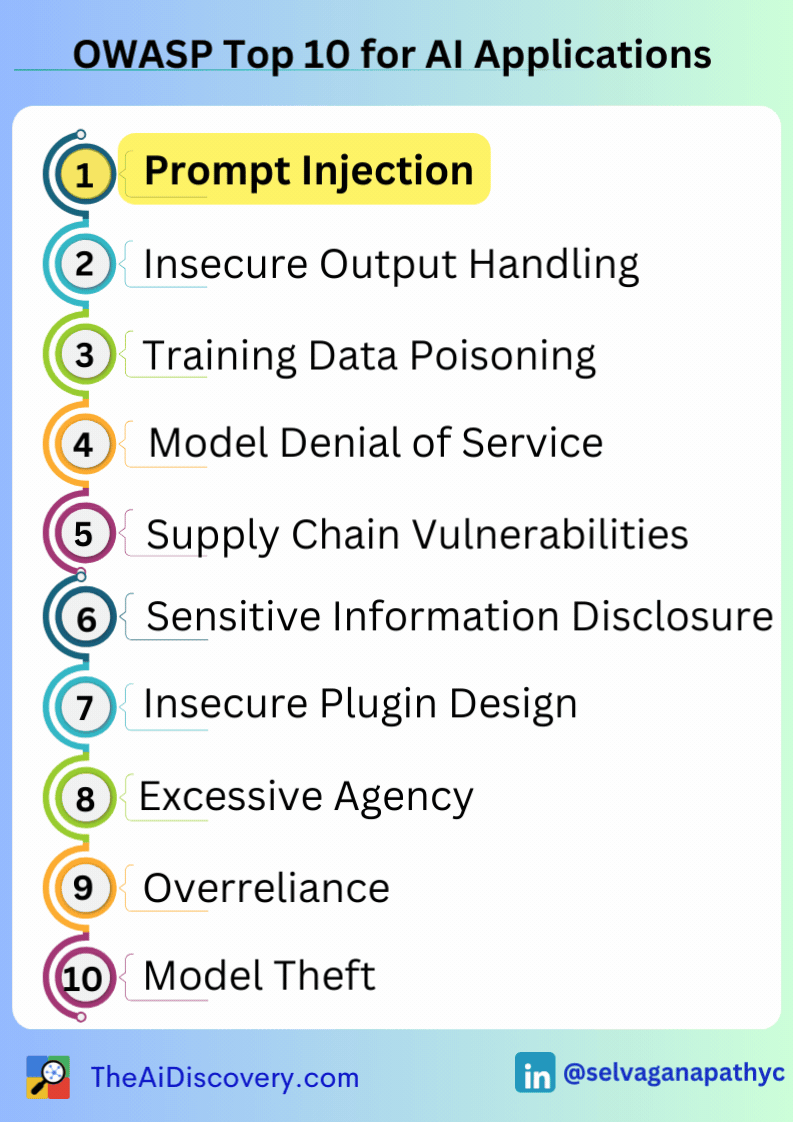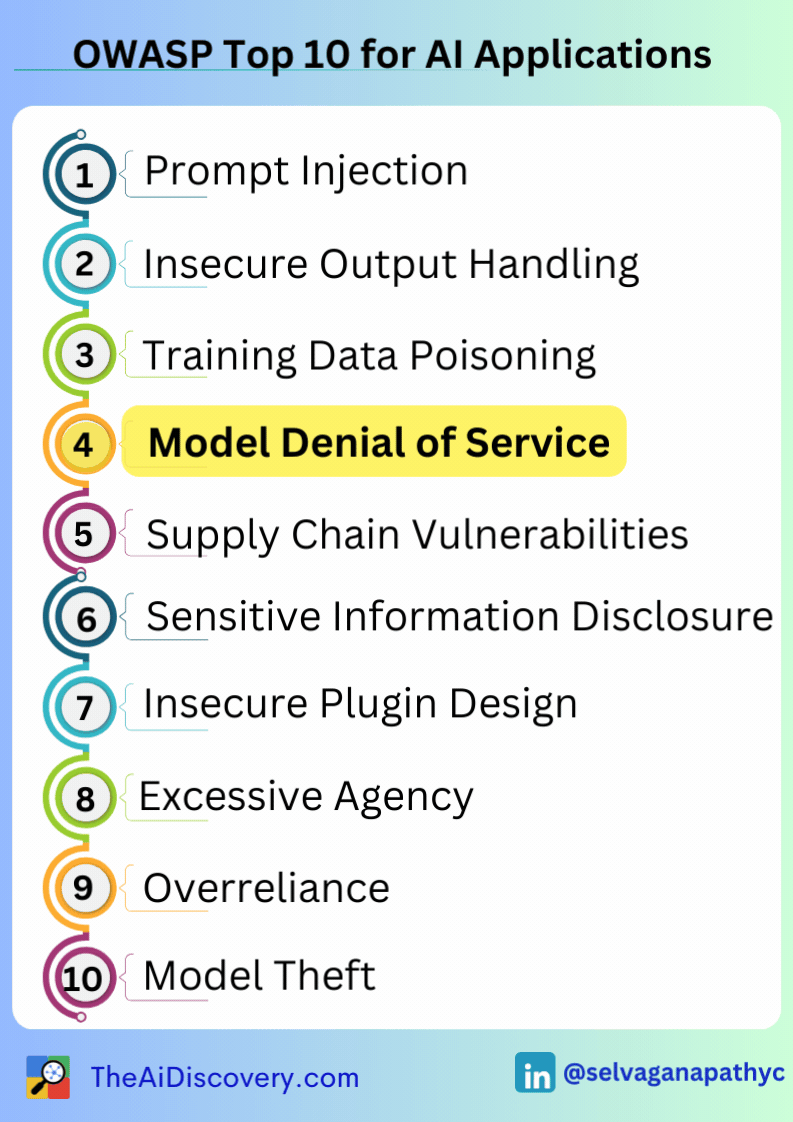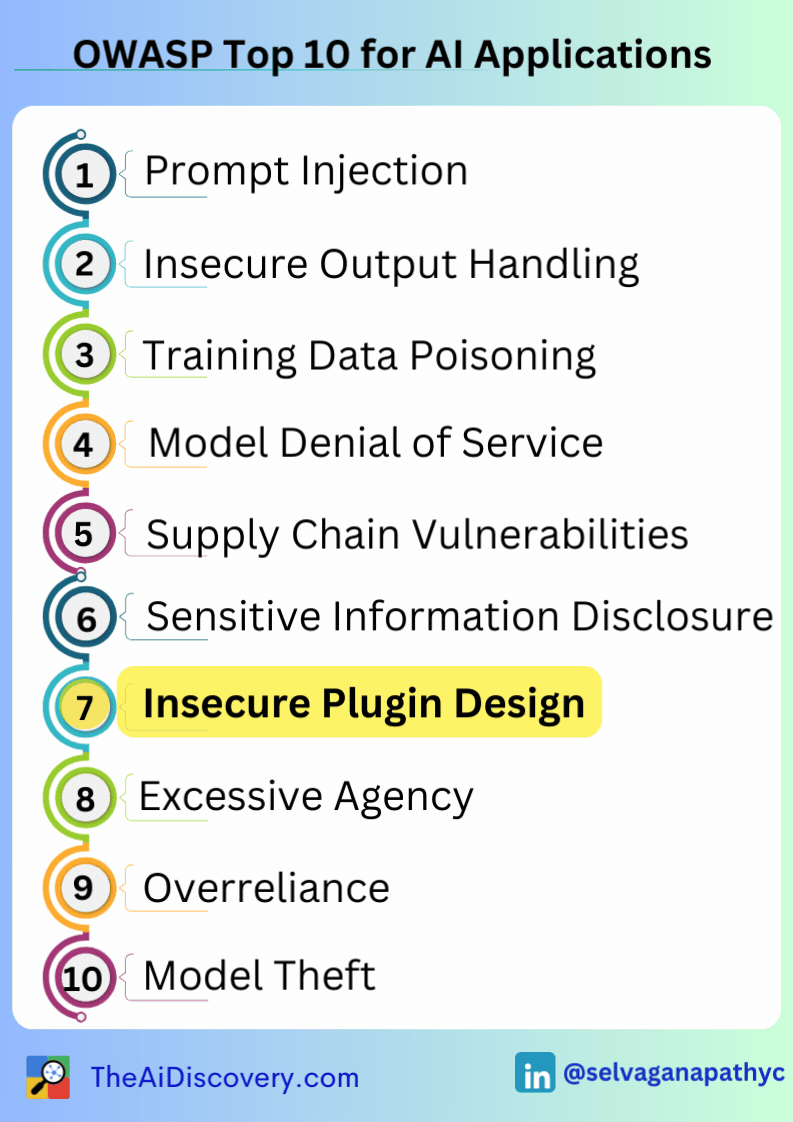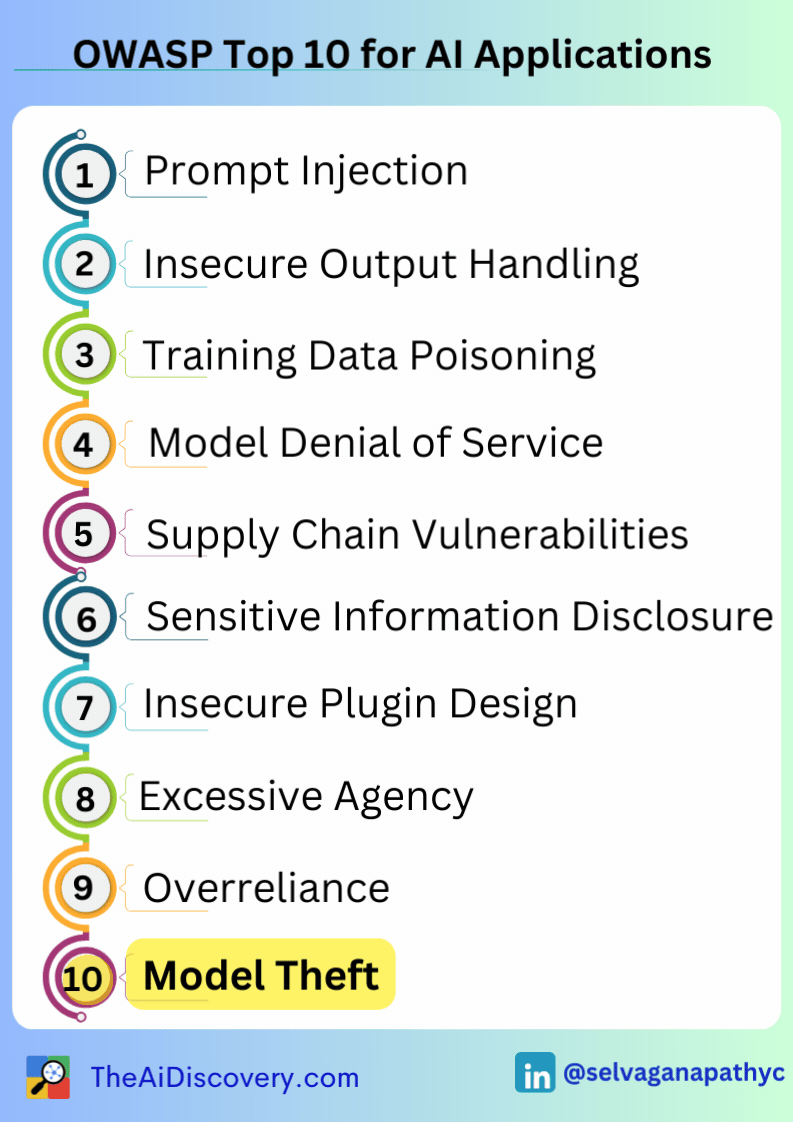
Then I discovered the 𝗢𝗪𝗔𝗦𝗣 𝗧𝗼𝗽 𝟭𝟬 𝗳𝗼𝗿 𝗟𝗮𝗿𝗴𝗲 𝗟𝗮𝗻𝗴𝘂𝗮𝗴𝗲 𝗠𝗼𝗱𝗲𝗹 𝗔𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻𝘀 project, which provides a crucial resource for understanding and mitigating these vulnerabilities. The top 10 most critical vulnerabilities include:
𝗪𝗵𝗼 𝗦𝗵𝗼𝘂𝗹𝗱 𝗖𝗮𝗿𝗲?
All stakeholders involved in this AI Engineering space to design, develop and manage AI applications - Developers, Data Scientists, Security Experts, Business Leaders.
𝗪𝗵𝘆 𝗦𝗵𝗼𝘂𝗹𝗱 𝗬𝗼𝘂 𝗖𝗮𝗿𝗲?
𝗣𝗿𝗼𝘁𝗲𝗰𝘁 𝗦𝗲𝗻𝘀𝗶𝘁𝗶𝘃𝗲 𝗜𝗻𝗳𝗼𝗿𝗺𝗮𝘁𝗶𝗼𝗻: Avoid leaks of confidential and proprietary data.
𝗠𝗮𝗶𝗻𝘁𝗮𝗶𝗻 𝗧𝗿𝘂𝘀𝘁: Ensure clients and users trust your AI applications by demonstrating a strong commitment to security.
𝗖𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲: Meet regulatory requirements
𝗢𝗽𝗲𝗿𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝗖𝗼𝗻𝘁𝗶𝗻𝘂𝗶𝘁𝘆: Prevent disruptions caused by security incidents, such as denial of service attacks or data poisoning.
By following the OWASP Top 10 for AI applications, we can significantly enhance the security posture of our AI projects. This list is not just a guideline but a crucial tool for ensuring that the powerful capabilities of AI models are harnessed safely and responsibly.